

EXPLORE.PERSIST.MASTER.
CompTIA PenTest+.
Share :
+971 43346660
CompTIA PenTest+ is a certification for intermediate level cybersecurity professionals who are tasked with penetration testing to identify, exploit, report, and manage vulnerabilities on a network.
PenTest+ assesses the most up-to-date penetration testing, and vulnerability assessment and management skills necessary to determine the resiliency of the network against attacks. Successful candidates will have the intermediate skills and best practices required to customize assessment frameworks to effectively collaborate on and report findings, and communicate recommended strategies to improve the overall state of IT security.
PenTest+ is compliant with ISO 17024 standards and approved by the US DoD to meet directive 8140/8570.01-M requirements. Regulators and government rely on ANSI accreditation, because it provides confidence and trust in the outputs of an accredited program. Over 2.3 million CompTIA ISO/ANSI-accredited exams have been delivered since January 1, 2011.
Required Exam: PT0-002
Target Audience:
- Information Security Analyst / Administrator
- Information Assurance (IA) Security Officer
- Information Security Manager / Specialist
- Information Systems Security Engineer / Manager
- Information Security Professionals / Officers
- Information Security / IT Auditors
- Risk / Threat/Vulnerability Analyst
- System Administrators
- Network Administrators and Engineer
Prerequisite:
While there is no required prerequisite, PenTest+ is intended to follow CompTIA Security+ or equivalent experience and has a technical, hands-on focus.
-
- Key issues include plaguing the information security world, ethical hacking, information security controls, laws, and standards.
- Perform footprinting and reconnaissance using the latest footprinting techniques and tools as a critical pre-attack phase required in ethical hacking.
- Network scanning techniques and scanning countermeasures. Enumeration techniques and enumeration countermeasures.
- Vulnerability analysis to identify security loopholes in the target organization’s network, communication infrastructure, and end systems.
- System hacking methodology, steganography, steganalysis attacks, and covering tracks to discover system and network vulnerabilities.
- Different types of malware (Trojan, Virus, worms, etc.), system auditing for malware attacks, malware analysis, and countermeasures.
- Packet sniffing techniques to discover network vulnerabilities and countermeasures to defend sniffing.
Duration
40 Hours
Skill Level
Beginner
Certificate
Yes
Modules
5
Language
English
Mode
Online/Offline
Key Highlights
- Live Instructor-Led Training (Online & Classroom)
- 40 Hours of Technology Lectures
- Weekdays (Tue - Fri)
- Friday to Saturday or Saturday to Sunday - Weekend
- Real World Live Scenarios and Migrations
- Exam question bank and Preparation
Key Highlights
- 100% Pass Guarantee
- 24/7 Access to the Learning Resources
- Hands-on Lab Practice on physical equipment
- Flexible Installment Plans
- Boot Camp Training for a Fast Track Learning
- Demand-driven recorded video lectures for references
- Eve-ng Set up on the laptop with images
Course Curriculam
- Explain the importance of planning for an engagement.
- Explain key legal concepts.
- Explain the importance of scoping an engagement properly.
- Explain the key aspects of compliance-based assessments.
- Given a scenario, conduct information gathering
- using appropriate techniques.
- Given a scenario, perform a vulnerability scan.
- Given a scenario, analyze vulnerability scan results.
- Explain the process of leveraging information
- to prepare for exploitation.
- Explain weaknesses related to specialized systems.
- Compare and contrast social engineering attacks.
- Given a scenario, exploit network-based vulnerabilities.
- Given a scenario, exploit wireless and RF-based vulnerabilities.
- Given a scenario, exploit application-based vulnerabilities.
- Given a scenario, exploit local host vulnerabilities.
- Summarize physical security attacks related to facilities.
- Given a scenario, perform post-exploitation techniques.
- Summarize physical security attacks related to facilities.
- Given a scenario, perform post-exploitation techniques.
- Given a scenario, use Nmap to conduct information gathering exercises.
- Compare and contrast various use cases of tools.
- Given a scenario, analyze tool output or
- data related to a penetration test.
- Given a scenario, analyze a basic script
- (limited to Bash, Python, Ruby, and PowerShell).
- Given a scenario, use report writing and handling best practices.
- Explain post-report delivery activities.
- Given a scenario, recommend mitigation
- strategies for discovered vulnerabilities.
- Explain the importance of communication
- during the penetration testing process.
lab infrastructure.

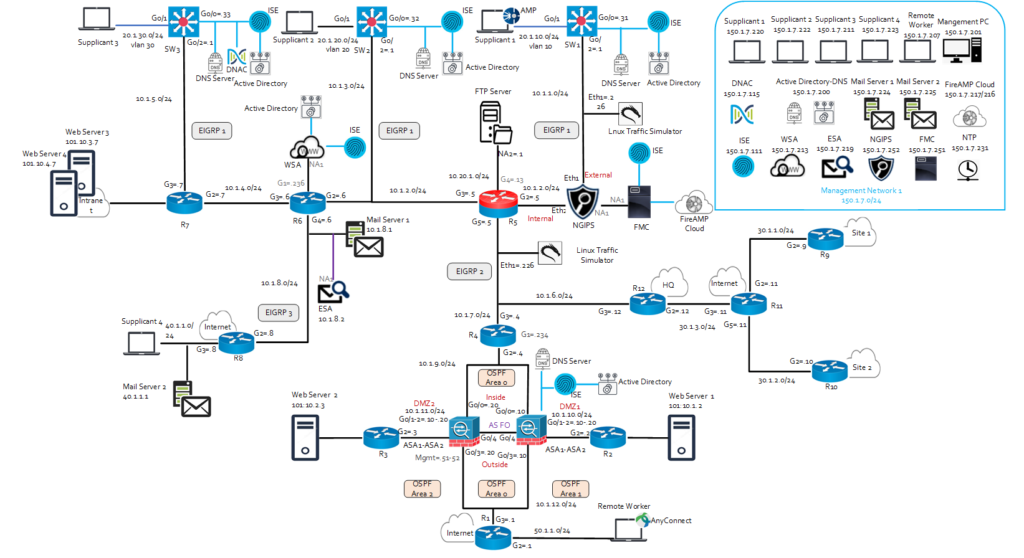
CCIE enterprise infrastructure v1.1 equipment and software list:


The practical exam tests candidates on solutions that can be configured using the below
Equipment and software versions. Candidates may see more recent software versions
during their attempt but will only be tested on features that are supported in the list below.
Passing the exam requires a depth of understanding difficult to obtain without hands-on
experience. Early in your preparation you should arrange access to equipment and soft-
ware similar to that used on the exam.
Virtual machines
- Cisco Catalyst 8000V Routers with Cisco IOS XE Software Release 17.9
- Cisco IOSv with Cisco IOS Software Release 15.8
- Cisco IOSv-L2 with Cisco IOS Software Release 15.2
- Cisco SD-WAN (vManage, vBond, vSmart, cEdge) Software Release 20.9
- Cisco DNA Center, Release 2.3

Physical Equipment
- Cisco Catalyst 9300 Switches with Cisco IOS XE Software Release 17.9 Other (supporting virtual machines)
- Cisco Identity Services Engine 3.1
- Linux Desktop
Topology

Modes Of Training
We provide various modes of training, each catering to different learning styles, preferences, and needs.You can make your choice of training mode.
- Classroom-Based Training
- One-On-One Training
- Online Training
- Corporate Training
- Fast Track Training
- Private Group Training
- Lab Workshop Training
Instructors
MCSE,RHCE,CCNP,CEH,CSA,CCSE,F5-CTS, AWS & Azure
Certified instructor with 20+ years of experience in the field of cloud and cybersecurity. Proven success in leveraging educational theories and methodologies to design, develop, and deliver successful training programs and integrate instructional technology to provide onsite and virtual training. Babu has helped IPRULERS in setting the bar for cloud and cyber security training and helping thousands of engineers to obtain their own certifications. He excels in corporate training and has excellent interpersonal skills that make him stand out. Babu has proven his knowledge and skills in delivering training for the Microsoft, Amazon, f5, Check Point, EC-Council, CompTIA & Cisco etc.

Babu Varghese
Senior Cloud & Security Specialist




