

EXPLORE.PERSIST.MASTER.
Palo Alto Networks Certified Network Security Administrator (PCNSA)Training.
Share :
+971 43346660
The Palo Alto Networks Certified Network Security Administrator certification is designed for IT professionals who can demonstrate a detailed knowledge of core features and functions of Palo Alto Networks next-generation firewalls. We are offering in-depth knowledge in the Palo Alto Networks Certified Network Security Administrator (PCNSA) field through our special designed training course. Palo Alto Networks Certified Network Security Administrator (PCNSA) can operate Palo Alto Networks next-generation firewalls to protect networks from cutting edge cyber threats. PCNSA certification validates your ability to configure the central features of Palo Alto Networks Next Generation Firewall and capability to effectively deploy the firewalls to enable network traffic based on who (User-ID), what (App-ID), and when (Policy), all while ensuring security (Content-ID).
IPRulers is the new face of Security Certification and Training in Dubai, UAE, which provides both online and classroom-based training in the latest cutting-edge fundamental technologies in the IT sector. With grouped as well as one-to-one classes and online tutorials that could be scheduled for weekdays or weekends in accordance to the students’ choice, IPRulers is fast becoming a leading name in Dubai in providing a highly valued Cisco Certificate, with a 100% pass rate on the first attempt. Successful completion of this five-day, instructor-led course should enhance the student’s understanding of how to configure and manage Palo Alto Networks next-generation firewalls. The student should learn and get hands-on experience configuring, managing, and monitoring a firewall in a lab environment, all with the help of IPRulers.
Target Audience:
- Security Engineers,
- Security Administrators,
- Security Operations Specialists,
- Security Analysts, and Support Staff
Prerequisite:
There are no prerequisites but knowledge basic networking is an advantage.
Recommended Training:
Firewall 11.0 Essentials:
Configuration and Management (EDU-210) Training
PCNSA certification validates your ability to configure the central features of Palo Alto Networks Next Generation Firewall and capability to effectively deploy the firewalls to enable network traffic based on who (User-ID), what (App-ID), and when (Policy), all while ensuring security (Content-ID).
Required Exam : PCNSA
Duration
40 Hours
Skill Level
Intermediate
Certificate
Yes
Modules
4
Language
English
Mode
Online/Offline
Key Highlights
- Live Instructor-Led Training (Online & Classroom)
- 40 Hours of Technology Lectures
- Weekdays (Tue - Fri)
- Friday to Saturday or Saturday to Sunday - Weekend
- Real Equipment and Real World Live Scenarios
- Exam question bank and Preparation
Key Highlights
- 100% Pass Guarantee
- 24/7 Access to the Learning Resources
- Hands-on Lab Practice on physical equipment
- Flexible Installment Plans
- Boot Camp Training for a Fast Track Learning
- Demand-driven recorded video lectures for references
- Training & Practice on Physical and Licensed Equipment
Course Curriculam
Domain Weight(%)
Device Management and Services 22%
Managing Objects 20%
Policy Evaluation and Management 28%
Securing Traffic 30%
Course Content
1.Demonstrate knowledge of firewall management interfaces.
1.1.1 Management interfaces
1.1.2 Methods of access
1.1.3 Access restrictions
1.1.4 Identity-management traffic flow
1.1.5 Management services
1.1.6 Service routes
1.2 Provision local administrators
1.2.1 Authentication profile
1.2.2 Authentication sequence
1.3 Assign role-based authentication
1.4 Maintain firewall configurations
1.4.1 Running configuration
1.4.2 Candidate configuration
1.4.3 Discern when to use load, save, import, and export
1.4.4 Differentiate between configuration states
1.4.5 Back up Panorama configurations and firewalls from Panorama
1.5 Push policy updates to Panorama-managed firewalls
1.5.1 Device groups and hierarchy
1.5.2 Where to place policies
1.5.3 Implications of Panorama management
1.5.4 Impact of templates, template stacks, and hierarchy
1.6 Schedule and install dynamic updates
1.6.1 From Panorama
1.6.2 From the firewall
1.6.3 Scheduling and staggering updates on an HA pair
1.7 Create and apply security zones to policies
1.7.1 Identify zone types
1.7.2 External types
1.7.3 Layer 2
1.7.4 Layer 3
1.7.5 TAP
1.7.6 VWire
1.7.7 Tunnel
1.8 Identify and configure firewall interfaces
1.8.1 Different types of interfaces
1.8.2 How interface types affect Security policies
1.9 Maintain and enhance the configuration of a virtual or logical router
1.9.1 Steps to create a static route
1.9.2 How to use the routing table
1.9.3 What interface types can be added to a virtual or logical router
1.9.4 How to configure route monitoring
2.1 Create and maintain address and address group objects
2.1.1 How to tag objects
2.1.2 Differentiate between address objects
2.1.3 Static groups versus dynamic groups
2.2 Create and maintain services and service groups
2.3 Create and maintain external dynamic lists
2.4 Configure and maintain application filters and application groups
2.4.1 When to use filters versus groups
2.4.2 The purpose of application characteristics as defined in the App-ID database
3.1 Develop the appropriate application-based Security policy
3.1.1 Create an appropriate App-ID rule
3.1.2 Rule shadowing
3.1.3 Group rules by tag
3.1.4 The potential impact of App-ID updates to existing Security policy rules
3.1.5 Policy usage statistics
Differentiate specific security rule types
3.2.1 Interzone
3.2.2 Intrazone
3.2.3 Universal
3.3 Configure Security policy match conditions, actions, and logging options
3.3.1 Application filters and groups
3.3.2 Logging options
3.3.3 App-ID
3.3.4 User-ID
3.3.5 Device-ID
3.3.6 Application filter in policy
3.3.7 Application group in policy
3.3.8 EDLs
3.4 Identify and implement proper NAT policies
3.4.1 Destination
3.4.2 Source
3.5 Optimize Security policies using appropriate tools
3.5.1 Policy test match tool
3.5.2 Policy Optimizer
4.1 Compare and contrast different types of Security profiles
4.1.1 Antivirus
4.1.2 Anti-Spyware
4.1.3 Vulnerability Protection
4.1.4 URL Filtering
4.1.5 WildFire Analysis
4.2 Create, modify, add, and apply the appropriate Security profiles and groups
4.2.1 Antivirus
4.2.2 Anti-Spyware
4.2.3 Vulnerability Protection
4.2.4 URL Filtering
4.2.5 WildFire Analysis
4.2.6 Configure threat prevention policy
4.3 Differentiate between Security profile actions
4.4 Use information available in logs
4.4.1 Traffic
4.4.2 Threat
4.4.3 Data
4.4.4 System logs
4.5 Enable DNS Security to control traffic based on domains
4.5.1 Configure DNS Security
4.5.2 Apply DNS Security in policy
4.6 Create and deploy URL-filtering-based controls
4.6.1 Apply a URL profile in a Security policy
4.6.2 Create a URL Filtering profile
4.6.3 Create a custom URL category
4.6.4 Control traffic based on a URL category
4.6.5 Why a URL was blocked
4.6.6 How to allow a blocked URL
4.6.7 How to request a URL recategorization
4.7 Differentiate between group mapping and IP-to-user mapping
within policies and logs
4.7.1 How to control access to specific locations
4.7.2 How to apply to specific policies
4.7.3 Identify users within the ACC and the monitor tab
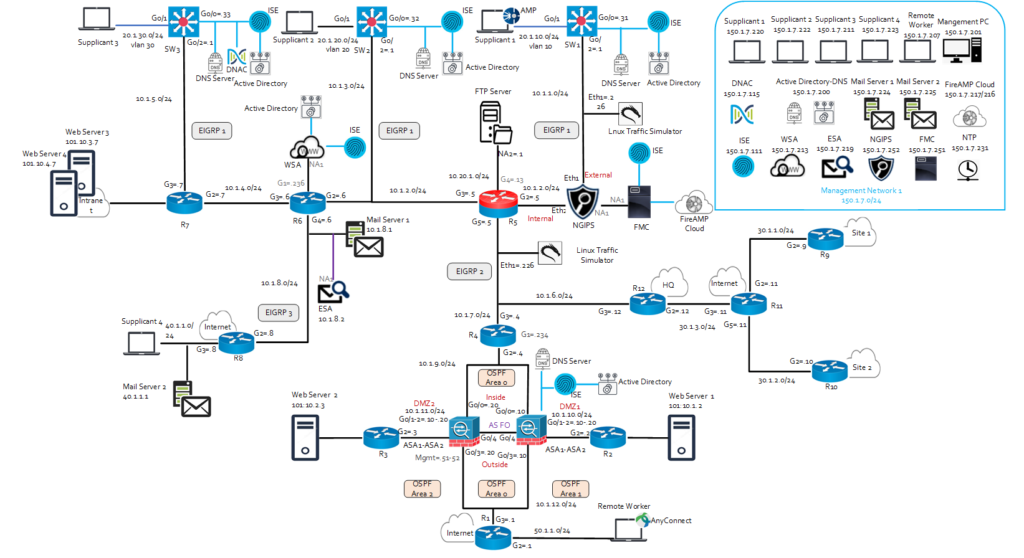
lab infrastructure.
IPRulers has a fully equipped Palo Alto network lab, specially designed for the PCNSA,
PCNSE training, with an enhanced lab topology that represent real world network. Students
will have the following equipment and software configured for their training; they may also
get the chance to see newer hardware and software during this period.

Palo Alto Networks Equipment and Software List


Palo Alto Networks technology is highly integrated and automated. The Palo Alto Networks product portfolio comprises multiple separate technologies working in unison to prevent successful cyberattacks. Those who earn the Palo Alto Networks Certified Network Security Administrator (PCNSA) certification demonstrate their ability to operate the Palo Alto Networks firewall to protect networks from cutting-edge cyberthreats.
Physical Equipment
- Palo Alto Networks PA-220
- Palo Alto Networks PA-440

Virtual Machines
- Palo Alto Networks VM-50
- Palo Alto Networks PAN-OS 11.0
- Palo Alto Networks Panorama Virual Appliance 11.0
Supporting Machines
- TEST PC: WINDOWS 10
- AD/DNS/CA: WINDOW SERVER 2016
- LINUX KALI
Topology

Modes Of Training
We provide various modes of training, each catering to different learning styles, preferences, and needs.You can make your choice of training mode.
- Classroom-Based Training
- One-On-One Training
- Online Training
- Corporate Training
- Fast Track Training
- Private Group Training
- Lab Workshop Training
Instructors

MD & Founder
4XCCIE (R&S, Security, Collaboration, DC), PCNSE & NSE7
Gigi Vikraman a quadruple CCIE has over 15 years of experience working in the Cisco networking field consulting and training. In addition, he has designed, implemented and supported numerous enterprise networks. He has been a dedicated CCIE instructor for over 10 years. He has extended his service in producing 400+ CCIE’s all over the world. Apart from all these, he has already proven his well knowledge in giving training on Fortinet, Palo Alto and Check Point.




