

EXPLORE.PERSIST.MASTER.
Software Defined Access(SDA).
Share :
+971 43346660
Discover the comprehensive Cisco SDA Training offered by IPRULERS, designed to equip you with the expertise to seamlessly deploy the Cisco Software-Defined Access (SD-Access) solution within your enterprise network. Our hands-on, instructor-led course delves into SD-Access fundamentals, provisioning, policies, integration, border operations, and migration strategies. Explore the pivotal role of Cisco SD-Access within the Cisco Digital Network Architecture (Cisco DNA), addressing network change drivers, automation, and security. Gain proficiency in leveraging Cisco DNA Center and integrating it with Cisco ISE for streamlined endpoint management. Develop skills in operating and troubleshooting Cisco SD-Access networks, extending policies to WANs and data centers, and optimizing performance through Cisco DNA Assurance. By the conclusion of our training, you’ll possess the capabilities to effectively implement, operate, and troubleshoot SD-Access, elevating security and network management across your organization’s campus networks with IPRULERS
The Cisco Software-Defined Access (SD-Access) solution caters to a diverse audience within the IT landscape. For IT management, it offers insights into addressing key business requirements with enhanced efficiency and flexibility in network service delivery. Solution architects gain a deeper understanding of how SD-Access facilitates efficiency and flexibility for network services in the context of IT solution delivery.
Target Audience
- IT management, to understand how to address key business requirements with greater efficiency and flexibility in network service delivery
- IT solution architects, to understand the role that SDA plays in enabling such efficiency and flexibility for network services in the context of IT solution delivery
- IT and network security architects, to understand how the integrated capabilities of the SDA solution are used to design and implement network segmentation-based security
- IT operations engineers, integrating network and application visibility and root cause analysis into integrated IT case handling workflows
- Networking Admin and Operations installing, integrating, configuring and operating Cisco DNA Center, Cisco Identity Services Engine (ISE), and other solution components, in the context of Cisco SDA based network services
- Networking Field Engineers using capabilities of Cisco DNA Center to deploy, monitor and maintain network infrastructure for SDA based network services
- Articulate the value of Cisco SDA Use Cases including, for example: saving operational and management cost to maintain and support ever growing network infrastructure; central security policy to comply to regional or global regulatory requirements and enterprise security policy; deliver best-in-class services to end-users; leveraging networking insights and trends to optimize business process and workflows.
- Describe the technical capabilities of Cisco DNA Center and how they are applied in SDA Use Cases. This includes the lifecycle stages of network device discovery, assigning network devices to sites, network design options, provisioning, software image management, building a fabric, segmentation design, assurance, application policy, etc.
- Set up an SDA environment, integrating Cisco Identity Services Engine (ISE) and other solution components as required.
- Apply troubleshooting methods, processes, tips to resolve implementation and maintenance issues of the following aspects of the technical solution
- Device Onboarding, including device discovery, Plug-and-Play and LAN Automation
- Network design settings, including sites, AAA, SNMP, Syslog, IP address pools, image management, network profiles, and authentication templates
Duration
40 Hours
Skill Level
Expert
Certificate
Yes
Modules
14
Language
English
Mode
Online/Offline
Key Highlights
- Live Instructor-Led Training (Online & Classroom)
- 40 Hours of Technology Lectures
- Weekdays (Tue - Fri)
- Weekend (Fri-Sat or Sat-Sun)
- Real World Live Scenarios and Migrations
- Exam question bank and Preparation
Key Highlights
- 100% Pass Guarantee
- 24/7 Access to the Learning Resources
- Hands-on Lab Practice on physical equipment
- Flexible Installment Plans
- Boot Camp Training for a Fast Track Learning
- Demand-driven recorded video lectures for references
Course Curriculam
- Understanding Cisco Intent-Based Networking
- Understanding Cisco SDA Use Cases customer’s benefits including business and technical outcomes and capabilities
- Cisco DNA Center Introduction
- SD-Access Overview
- SD-Access Benefits
- SD-Access Key Concepts
- SD-Access Main Components
➡️DNA Controller
➡️NDP (Analytics and Assurance) - Cisco DNA Center Automation
- Cisco ISE (Policy)
- Cisco StealthWatch (Traffic Analysis)
- DNA Center Assurance
- SD-Access Campus Fabric Overview
- Key Components
➡️Control Plane Based on LISP
➡️Data Plane Based on VXLAN
➡️Policy Plane Based on CTS - Cisco SD-Access Platform Support
➡️Fabric Edge Node
➡️Fabric Control Plane
➡️Fabric Border Node
➡️Fabric Extended Node - Fabric-Enabled WLAN
- Cisco SD-Access Scaling Considerations
- Cisco DNA-Center Appliances
- Cisco DNA-Center Deployment Models
➡️Single Node Deployment
➡️Clustered Deployment - Installation Procedure
- Initial Setup and Configuration
- GUI Navigation
- Network design options
- Sites
- Creating Enterprise and Sites Hierarchy
- Configuring General Network Settings
- Loading maps into the GUI
- IP Address Management
- Software Image Management
- Network Device Profiles
- AAA
- SNMP
- Syslog
- IP address pools
- Image management
- Creating Enterprise and Guest SSIDs
➡️Creating the wireless RF Profile
➡️Creating the Guest Portal for the Guest SSIDs - Network profiles
- Authentication templates
- 2-level Hierarchy
➡️Macro Level: Virtual Network (VN)
➡️Micro Level: Scalable Group (SG) - Policy
➡️Policy in SD-Access
➡️Access Policy: Authentication and Authorization
➡️Access Control Policy
➡️Application Policy
➡️Extending Policy across domains
➡️Preserving Group Metadata across Campus, WAN and DC
➡️Enforcing policy in Firewall domains
➡️Cross Domain Policies
- Devices Onboarding
➡ Lifecycle stages of network device discovery
➡Discovering Devices
➡Assigning Devices to a site
➡️Provisioning device with profiles
➡️Plug-and-Play
➡️LAN Automation
➡️Templates
➡️Templates for day 0
➡️Templates for day N operations - IP Transits
➡️How to connect the Fabric Sites to the external network
➡️Creating the IP Transit
➡️Considerations for a SD-Access Border Node Design
➡️BGP Hand-Off Between Border and Fusion - Fabric Domains
➡️Understanding Fabric Domains and Sites
➡️Using Default LAN Fabric Domain
➡️Creating Additional Fabric Domains and Sites - Adding Nodes
➡️Adding Fabric Edge Nodes
➡️Adding Control Plane Nodes
➡️Adding Border Nodes
- Overview of DNA Assurance
- Cisco DNA Center Assurance- Use Cases Examples
- Network Health & Device 360
- Client Health & Client 360
- Application Health & Application 360
- Cisco SD- Application Visibility Control (AVC) on DNA-Center
- Proactive troubleshooting using Sensors
- Introduction to Cisco SD-Access Distributed Campus Design – The Advantage?
- Fabric Domain vs Fabric Site
- SD-Access Transits:
➡️IP-Based Transit
➡️Cisco SD-Access Transit
➡️Cisco SD-WAN Transit - Deploying the Cisco Distributed Campus with SD-Access Transit
➡️Site considerations
➡️Internet connectivity considerations
➡️Segmentation considerations
➡️Role of a Cisco Transit Control Plane - Cisco SD-Access Fabric in a Box
➡️The need for FiaB
➡️Deploying the FiaB
- Cisco SD-Access Migration Tools and Strategies
- Two Basic Approaches:
➡️Parallel Deployment Approach
➡️Incremental Deployment Approach
➡️Integration with existing Cisco ISE in the network – Things to watch out for! - Choosing the correct Fusion Device
➡️Existing Core as Fusion
➡️Firewall as Fusion - When do you need the SD-Access Layer-2 Border?
➡️L2 Border – Understanding the requirement
➡️Designing and Configuring the L2 Border
➡️L2 Border – Not a permanent solution
DAY0: Onboarding new devices using Zero Touch Deployment
DAY1: Configurations using Templates
DAYN: Security Advisories based on Machine Reasoning Engine
DAYN: Simplified Software Management based on Golden Images
DAYN: Defective Device Replacement – RMA
- ServiceNow
➡️Integration
➡️Management
Use Case: STACK LAN Automation
Use Case: Silent Hosts
Use Case: Wake on LAN
Use Case: The need for L2 flooding
Use Case: Multicast in the SD-Access Fabric
- Cisco SD-Access to ACI Integrations
➡️Phase-1: Policy Plane Integration
➡️Phase-2: Data Plane Integration - Cisco SD-Access to Cisco SD-WAN Integrations
➡️What is possible today? SD-WAN Transit setup.
➡️Phase-1: The one box solution
➡️Phase-2: The two box solution
- Fabric
- Layer 3 forwarding
- Layer 2 forwarding
- Multicast Forwarding
- Security in the Fabric
- Troubleshooting Multi-Site Deployments
Lab Outline
- Lab 1: SDA Fundamentals
- Lab 2: Using the DNAC Discovery Tool
- Lab 3: Using the DNAC Inventory Tool
- Lab 4: ISE and DNAC Integration
- Lab 5: Using the DNAC Design Application
- Lab 6: Using the DNAC Policy Application
- Lab 7: Fabric Provisioning
- Lab 8: Wired and Wireless Host and Access Point Onboarding Configuration
- Lab 9: Configuring External Connectivity Using Fusion Router
- Lab 10: Configuring Cisco ISE Policies for User Onboarding
- Lab 11: Onboarding and Provisioning Access Points
- Lab 12: Fabric and Segmentation Verification
- Lab 13: Layer-2 Border Fundamentals
- Lab 14: Configuring a Layer-2 Border to Extend the Same IP Pool
- Lab 15: Transitioning the Traditional User to the SDA Anycast Gateway
- Lab 16: Testing IP Connectivity between SDA User and Traditional User
- Lab 17: Introduction to SDA Distributed Campus
- Lab 18: Configuring an SDA-Transit and the Transit Control Plane (TCP)
- Lab 19: Designing a Second Fabric Site
- Lab 20: Deploying a Second Fabric Site – Fabric in a Box
- Lab 21: Deploying a New Fabric Edge using LAN Automation
- Lab 22: Automate Network Devices Using Day-N Template
- Lab 23: Add as Edge Node to Fabric Site-2
- Lab 24: Host Onboarding at Fabric Site-2
- Lab 25: Connecting the two Fabric Sites Using the SDA-Transit
- Lab 26: Testing IP Connectivity and Micro-Segmentation between Fabric Site-1 and Fabric Site-2
lab infrastructure.

Equipment List


The practical exam tests candidates on solutions that can be configured using the below
Equipment and software versions. Candidates may see more recent software versions
during their attempt but will only be tested on features that are supported in the list below.
Passing the exam requires a depth of understanding difficult to obtain without hands-on
experience. Early in your preparation you should arrange access to equipment and soft-
ware similar to that used on the exam.
Virtual machines
- Cisco Catalyst 8000V Routers with Cisco IOS XE Software Release 17.9
- Cisco IOSv with Cisco IOS Software Release 15.8
- Cisco IOSv-L2 with Cisco IOS Software Release 15.2
- Cisco SD-WAN (vManage, vBond, vSmart, cEdge) Software Release 20.9
- Cisco DNA Center, Release 2.3

Physical Equipment
- Cisco Catalyst 9300 Switches with Cisco IOS XE Software Release 17.9 Other (supporting virtual machines)
- Cisco Identity Services Engine 3.1
- Linux/Windows Desktop
- Cisco Catalyst 9100 Series Access Point
- Embedded - Catalyst 9800 on a Catalyst 9300 switch
Topology
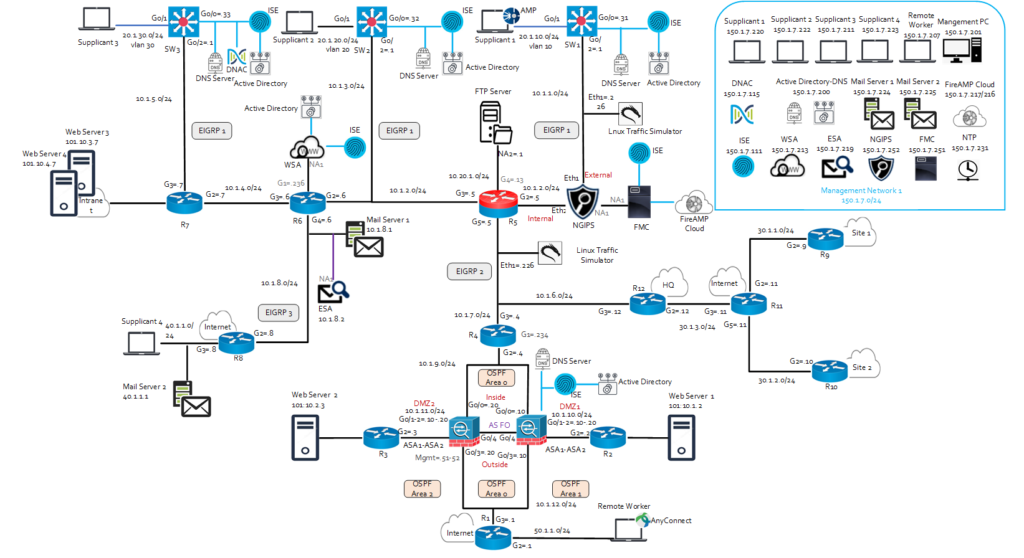

Modes Of Training
We provide various modes of training, each catering to different learning styles, preferences, and needs.You can make your choice of training mode.
- Classroom-Based Training
- One-On-One Training
- Online Training
- Corporate Training
- Fast Track Training
- Private Group Training
- Lab Workshop Training
Instructors
4XCCIE (R&S, Security, Collaboration, DC), PCNSE & NSE7
Gigi Vikraman a quadruple CCIE has over 15 years of experience working in the Cisco networking field consulting and training. In addition, he has designed, implemented and supported numerous enterprise networks. He has been a dedicated CCIE instructor for over 10 years. He has extended his service in producing 400+ CCIE’s all over the world. Apart from all these, he has already proven his well knowledge in giving training on Fortinet, Palo Alto and Check Point.

Gigi Vikraman
MD & FOUNDER




