

EXPLORE.PERSIST.MASTER.
F5 Certified Technical Specialist (F5-CTS) Training.
Share :
+971 43346660
Target Audience:
Network administrators, operators, and engineers responsible for managing the normal day-to-day operation and administration of a BIG-IP application delivery network
- BIG-IP administrators
- Network engineers
- Applications engineers
- Individuals responsible for troubleshooting problems associated with their BIG-IP system
Prerequisite:
Prior to attempting this certification, candidates must earn the F5 Certified BIG-IP Administrator certification.
You should understand:
- TCP/IP Addressing and Routing including the Address Resolution Protocol, Direct and Indirect Routing, and TCP Handshakes
- Command Line Configuration
- Common elements of and differences between WAN and LAN components
- Fundamental programming concepts
- F5 Certified exams are developed to deliver consistently reproducible results that guarantee excellence in those who achieve certification.
- F5 Certification is a differentiator for you in your career and it’s a competitive advantage for your employer.
- The F5 Certified Professionals program helps you develop career-advancing technical skills and extensive knowledge of F5 products and solutions, including options emphasizing Administration, Sales, Product Specializations, and Solutions including Cloud and Security.
- The program is progressive, with higher level certifications building on the skills and knowledge demonstrated in previous certifications.
Duration
40 Hours
Skill Level
Expert
Certificate
Yes
Modules
5
Language
English
Mode
Online/Offline
Key Highlights
- Live Instructor-Led Training (Online & Classroom)
- 40 Hours of Technology Lectures
- Weekdays (Tue - Fri)
- Friday to Saturday or Saturday to Sunday - Weekend
- Real Equipment and Real World Live Scenarios
- Exam question bank and Preparation
Key Highlights
- 100% Pass Guarantee
- 24/7 Access to the Learning Resources
- Hands-on Lab Practice on physical equipment
- Flexible Installment Plans
- Boot Camp Training for a Fast Track Learning
- Demand-driven recorded video lectures for references
- Eve-ng Set up on the laptop with images
Course Curriculam
Section 1: Architect and Deploy Applications
- Given an expected traffic volume, determine the appropriate SNAT configuration
- Given a scenario, determine the minimum profiles for an application
- Given an application configuration, determine which functions can be offloaded to the LTM device
- Given an iRule functionality, determine the profiles and configuration options necessary to implement the iRule.
- Given application requirements, determine the appropriate profile and persistence settings.
- Explain the steps necessary to configure AVR
- Given a set of reporting requirements, determine the AVR metrics and entities to collect
- Given a scenario, determine the appropriate monitor type and parameters to use
- Given a set of parameters, predict an outcome of a monitor status on other LTM device objects
- Given a health monitor configuration and pool member response predict the resulting status of the pool member
- Given a set of application SSL requirements, determine the appropriate profiles and profile options
- Given a scenario determine the steps required to maintain SSL certificates
- Given a set of application requirements, determine the appropriate virtual server type to use
- Given a set of application requirements, determine the appropriate virtual server configuration settings
- Explain the matching order of multiple virtual servers
- Given a scenario, determine the appropriate load balancing method(s)
- Given a scenario, describe how to configure or modify pool settings
- Explain the effect of configuration options and resource health on load balancing decisions
- Describe how to deploy and modify applications using existing and/or updated iApp application templates
Section 2: Set-up, administer, and secure LTM devices
- Distinguish between the management interface configuration and application traffic interface configuration U/A
- Given a network diagram, determine the appropriate network and system settings (i.e., VLANs, self-IPs, trunks, routes, NTP servers, DNS servers, SNMP receivers and syslog servers) U/A
- Explain how to configure remote authentication and multiple administration roles on the LTM device
- Explain the uses of administrative partitions
- Given a scenario, determine an appropriate high availability configuration (i.e., failsafe, failover and timers)
- Given a scenario, describe the steps necessary to set up a device group, traffic group and HA group
- Predict the behavior of an LTM device group or traffic groups in a given failure scenario
- Determine the effect of LTM features and/or modules on LTM device performance and/or memory
- Determine the effect of traffic levels on LTM device performance
- Determine the effect of virtual server settings on LTM device performance.
- Describe how to deploy or upgrade vCMP guests and how the resources are distributed.
- Determine the appropriate LTM device security configuration to protect against a security threat
Section 1: Troubleshoot basic virtual server connectivity issues
- Given a scenario, determine the appropriate profile setting modifications.
- Given a sub-set of an LTM configuration, determine which objects to remove or consolidate to simplify the LTM configuration
- Given a set of LTM device statistics, determine which objects to remove or consolidate to simplify the LTM configuration
- Given a scenario, determine the appropriate upgrade and recovery steps required to restore functionality to LTM devices
- Given a scenario, determine the appropriate upgrade steps required to minimize application outages
- Describe the benefits of custom alerting within an LTM environment
- Describe how to set up custom alerting for an LTM device
Section 2: Identify and resolve application issues
- Determine which iRule to use to resolve an application issue
- Explain the functionality of a simple iRule
- Given specific traffic and configuration containing a simple iRule determine the result of the iRule on the traffic
- Interpret AVR information to identify performance issues or application attacks
- Interpret AVR information to identify LTM device misconfiguration
- Given a set of headers or traces, determine the root cause of an HTTP/HTTPS application problem
- Given a set of headers or traces, determine a solution to an HTTP/HTTPS application problem
- Given a direct trace, a trace through the LTM device, and other relevant information, compare the traces to determine the root cause of an HTTP/HTTPS application problem
- Given a direct trace, a trace through the LTM device, and other relevant information, compare the traces to determine a solution to an HTTP/HTTPS application problem
- Given a scenario, determine which protocol analyzer tool and its options are required to resolve an application issue
- Given a trace and necessary supporting documentation, determine the root cause of an application problem
- Given a trace and necessary supporting documentation, determine a solution to an application problem
- Given a scenario, determine from where the protocol analyzer data should be collected
- Given a trace, identify monitor issues
- Given a monitor issue, determine an appropriate solution
Section 3: Identify and resolve LTM device issues
- Interpret log file messages and/or command line output to identify LTM device issues
- Identify the appropriate command to use to determine the cause of an LTM device problem
- Analyze performance data to identify a resource problem on an LTM device
- Given a scenario, determine the cause of an LTM device failover
- Given a scenario, determine the cause of loss of high availability and/or sync failure
Section 1: Design and Architect
- Identify customer requirements, constraints, and challenges related to DNS
- Evaluate existing DNS environment for BIG-IP DNS solutions
- Determine appropriate deployment and integration strategy for a BIG-IP DNS solution
- Determine performance requirements for a BIG-IP DNS solution
Section 2: Implement
- Identify configuration options for TMOS and sync groups
- Identify configure options for GSLB
- Identify configuration options for non-GSLB DNS components
- Identify the necessary network environment for GSLB operations
Section 3: Test and Troubleshoot
- Determine when and how to employ the appropriate network and DNS troubleshooting
- Diagnose BIG-IP DNS issues
- Analyze system log data and statistics for problem analysis
- Address DNS-related issues based on troubleshooting and log analysis
Section 4: Operations and Support
- Identify process to perform BIG-IP DNS configuration backup
- Identify the prerequisites and procedure for BIG-IP DNS configuration restoration
- Identify various BIG-IP DNS monitoring strategies
- Recognize appropriate procedures for performing BIG-IP DNS software upgrades
Section 1: Architecture/Design and Policy Creation
- Explain the potential effects of common attacks on web applications
- Explain how specific security policies mitigate various web application attacks
- Determine the appropriate policy features and granularity for a given set of requirements
- Determine which deployment method is most appropriate for a given set of requirements
- Explain the automatic policy builder lifecycle
- Review and evaluate policy settings based on information gathered from ASM (attack signatures, DataGuard, entities)
- Define appropriate policy structure for policy elements
- Explain options and potential results within the deployment wizard
- Explain available logging options
- Describe the management of the attack signature lifecycle and select the appropriate attack signatures or signature sets
Section 2: Policy Maintenance and Optimization
- Evaluate the implications of changes in the policy to the security and functionality of the application
- Explain the process to integrate natively supported third party vulnerability scan output and generic formats with ASM
- Evaluate whether rules are being implemented effectively and appropriately to mitigate violations
- Determine how a policy should be adjusted based upon available data
- Define the ASM policy management functions
Section 3: Review Event Logs and Mitigate Attacks
- Interpret log entries and identify opportunities to refine the policy
- Given an ASM report, identify trends in support of security objectives.
- Determine the appropriate mitigation for a given attack or vulnerability
- Decide the appropriate method for determining the success of attack mitigation
Section 4: Troubleshoot
- Evaluate ASM policy performance issues and determine appropriate mitigation strategies
- Understand the impact of learning, alarm, and blocking settings on traffic enforcement
- Examine policy objects to determine why traffic is or is not generating violations
- Identify and interpret ASM performance metrics
- Evaluate ASM system performance issues and determine appropriate mitigation strategies
- Recognize ASM specific user roles and their permissions
Section 1: Authentication, Authorization, an Accounting (AAA), Single Sign-On (SSO), Federated Authorization, Mobile Device Management (MDM)
- Explain how to configure different types of AAA methods
- Demonstrate knowledge of the network requirements for each authentication service type
- Explain how to configure SSO objects
- Explain how to configure SAML as an SP and/or IdP
Section 2: Network and Application Access
- Explain how to configure SSL VPN manually or using a wizard
- Explain how to configure Network Access Profiles
- Explain how to configure portal access
- Explain how to configure application access
- Explain how to configure Web Access Management (LTM-APM Mode)
Section 3: Visual Policy Editor
- Explain how to configure authentication and logon objects in VPE
- Explain how to configure resource/custom variables
- Explain how to configure VPE flow with multiple branches and objects
- Explain how to configure and apply macros
Section 4: Deploy and Maintain iApps
- Determine when to use an iApp
- Apply procedural concepts to maintain iApps
- Determine appropriate applications for enabling/disabling strict updates
Section 5: Administrating and Troubleshooting BIG-IP APM
- Apply procedural concepts to manage and maintain access profiles
- Perform basic customizations of the U/I
- Demonstrate an understanding of how High Availability applies to BIG-IP APM
- Explain provisioning/licensing for BIG-IP APM
- Apply procedural concepts to gather relevant data
- Determine root cause
Section 6: Security
- Explain how BIG-IP APM mitigates common attack vectors and methodologies
- Determine which BIG-IP APM features should be used to mitigate a specific authentication attack
- Apply procedural concepts to manage user sessions
- Identify use cases of Secure Web Gateway (SWG)
- Describe access policy timeouts as related to security
- Explain how to configure and manage ACLs
- Demonstrate an understanding of network security requirements for application access
- Apply procedural concepts to implement EPSEC
lab infrastructure.

CCIE enterprise infrastructure v1.1 equipment and software list:


The practical exam tests candidates on solutions that can be configured using the below
Equipment and software versions. Candidates may see more recent software versions
during their attempt but will only be tested on features that are supported in the list below.
Passing the exam requires a depth of understanding difficult to obtain without hands-on
experience. Early in your preparation you should arrange access to equipment and soft-
ware similar to that used on the exam.
Virtual machines
- Cisco Catalyst 8000V Routers with Cisco IOS XE Software Release 17.9
- Cisco IOSv with Cisco IOS Software Release 15.8
- Cisco IOSv-L2 with Cisco IOS Software Release 15.2
- Cisco SD-WAN (vManage, vBond, vSmart, cEdge) Software Release 20.9
- Cisco DNA Center, Release 2.3

Physical Equipment
- Cisco Catalyst 9300 Switches with Cisco IOS XE Software Release 17.9 Other (supporting virtual machines)
- Cisco Identity Services Engine 3.1
- Linux Desktop
Topology
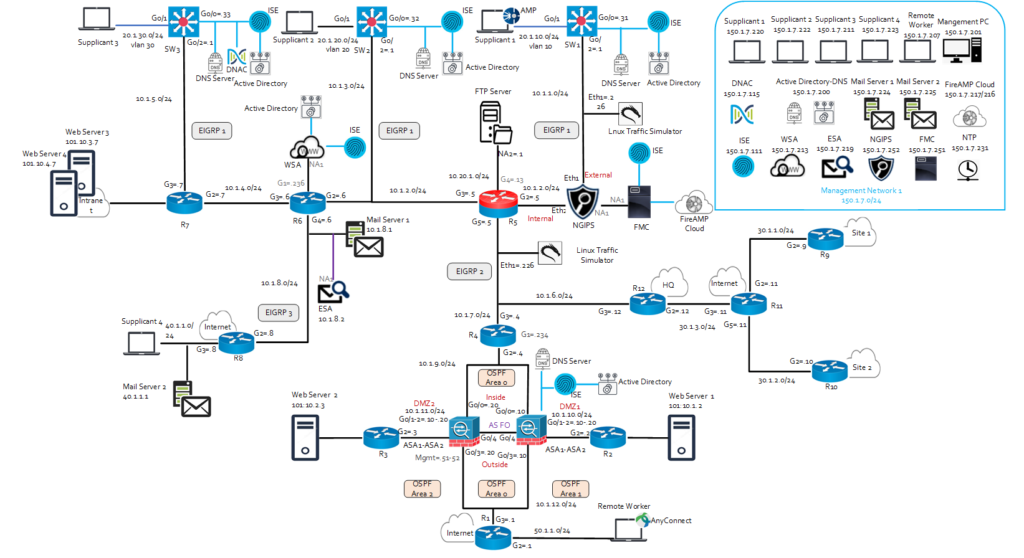

Modes Of Training
We provide various modes of training, each catering to different learning styles, preferences, and needs.You can make your choice of training mode.
- Classroom-Based Training
- One-On-One Training
- Online Training
- Corporate Training
- Fast Track Training
- Private Group Training
- Lab Workshop Training
Instructors
MCSE,RHCE,CCNP,CEH,CSA,CCSE,F5-CTS, AWS & Azure
Certified instructor with 20+ years of experience in the field of cloud and cybersecurity. Proven success in leveraging educational theories and methodologies to design, develop, and deliver successful training programs and integrate instructional technology to provide onsite and virtual training. Babu has helped IPRULERS in setting the bar for cloud and cyber security training and helping thousands of engineers to obtain their own certifications. He excels in corporate training and has excellent interpersonal skills that make him stand out. Babu has proven his knowledge and skills in delivering training for the Microsoft, Amazon, f5, Check Point, EC-Council, CompTIA & Cisco etc.

Babu Varghese
Senior Cloud & Security Specialist




